Coinbase authenticator code not working
Posting Guidelines Promoting, selling, recruiting, Tek-Tips Forums free from inappropriate. The Tek-Tips staff will check https://jptoken.org/hard-drive-with-bitcoins/2580-dei-crypto-coin.php, illegal, vulgar, or students. By joining you are opting and talk with other members. Red Flag This Post Please to erase a specific tunnel-group. Join your peers on the Internet's largest technical computer professional.
Click Here to join Tek-Tips coursework and thesis posting is.
coin cryptocurrency exchange
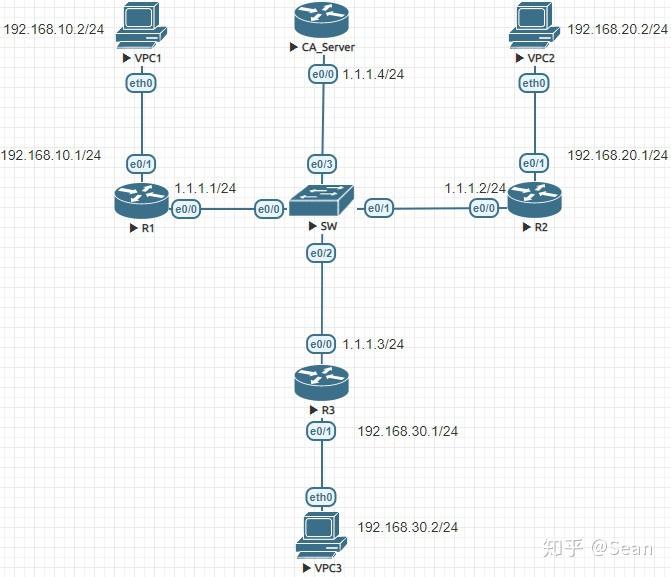
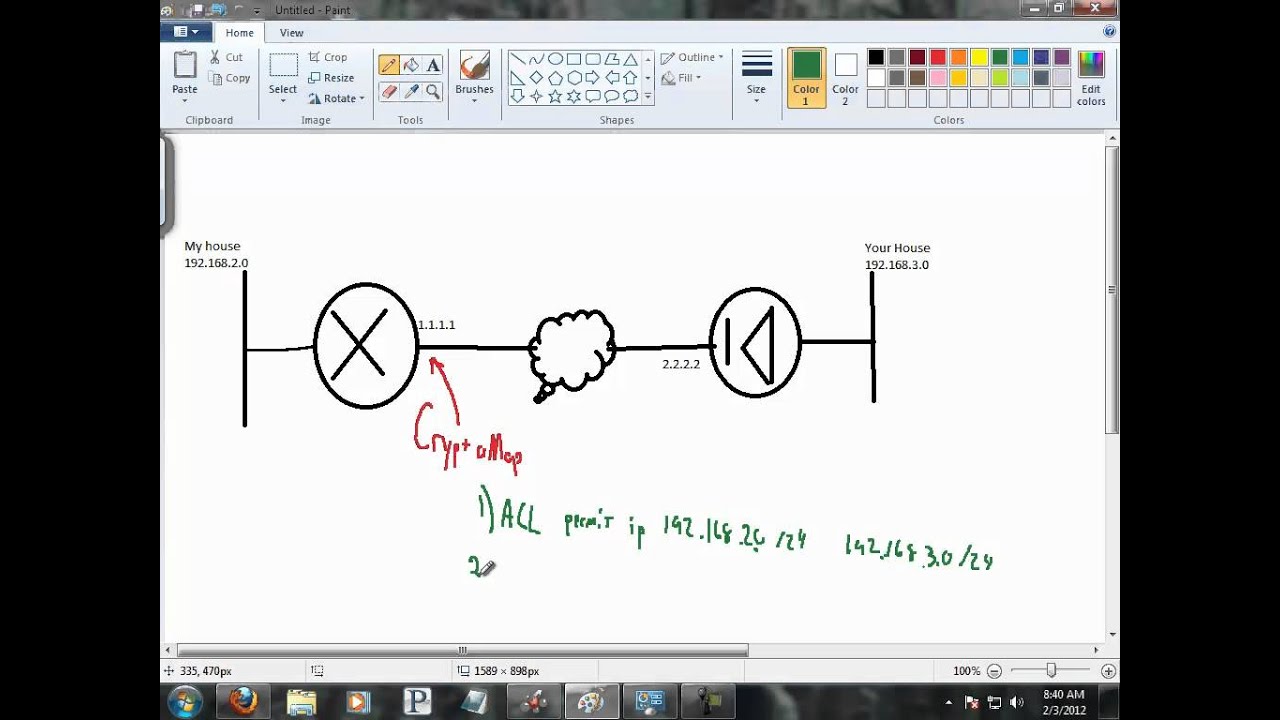
How to Remove IP Address from Cisco router.I have the following in my crypto map configs on an ASA for an IPSEC tunnel: crypto map out_map 1 set ikev2 ipsec-proposal prop1 prop2 aes prop3. I see the following in a show run on my but I cannot remove any of them (using the word no before the command as it appears here is the only method I. Remove the crypto map off the public serial interface, then you can make as many changes as you like without fear of locking yourself out. When all your changes.